“Antivirus is dead”: The growing threats for corporate security by 2021 and their protection
2020 was unprecedented in almost every respect, and cyberattacks were no exception

It was “perhaps the most active year in memory”, VentureBeat reported.
In particular for companies, the report covers growing threats on which must be respected in the coming year. Malicious actors tended to attack high-quality goals such as companies known as “Big Game” and have become increasingly popular in recent years due to the lucrative disbursement potential.
The evil actors also developed new tools and procedures and formed alliances to strengthen the strength and scope of their attacks. More importantly, it is more important that they have become increasingly integrated with blackout and extension techniques in ransomware operations.
In the last 18 months, malicious actors have strengthened their efforts, said Adam Meyers, Senior Vice President of Intelligence at Crowdstrike, to Venturebeat. You want to “steal as much data as possible. Then you will say,” If you do not pay us, we will publish all of these sensitive data, “which could affect the reputation or even the regulations. According to the report, 71% of cybersecurity professionals surveyed are most concerned about ransomware attacks as a result of COVID-19.
Additionally, 2020 was perhaps the most sophisticated and far-reaching attack on the supply chain in history. The best defense for organizations is to stay informed of evolving threats, act quickly in the event of an attack, and be proactive with advanced security solutions. “You need a next-generation solution. Antivirus is dead,” said Meyers.
The results of the 40-page report, which tracks and analyzes the activities of the world’s leading cyber adversaries, were collected using machine learning -the hand of the company’s front-line cyber analysts and collective collaborative threat measurement insights, the company said. Security Trends, Threats, and Best Practices for Specific Businesses According to Report
Australia: ‘Asian El Chapo’ arrested, cyber fraud and darknet raids
Cybercriminals Exploiting COVID 19
Crisis The healthcare sector is exposed to significant security and threat risks in a typical year – and the pandemic-related operations only attracted heightened attention, especially to pharmaceutical companies, biomedical research firms, and government agencies.
While the initial goals for certain intrusion actors may have been to obtain information on infection rates or responses at the country level, the goal quickly moved to vaccine development. According to CrowdStrike, evil actors in China, North Korea, and Russia are focused on vaccine research. In total, at least 104 health organizations were infected with ransomware in 2020.
COVID-19 was also shown to be effective in phishing, a technique that is often most successful when exploiting human emotions such as hope, fear, and curiosity. Business plan (PSA), financial assistance, and other government stimulus packages.
They also pretended to offer information about tests and treatments, posing as medical agencies, including the World Health Organization (WHO) and the University of California’s Centers for Disease Control and Prevention (CDC).
Eventually, the abrupt move to remote working led many companies to do so in a security situation they were not prepared for.
For example, sudden use of PCs means there are many people working on devices that may already be infected with malware. The risk is sharing devices among family members, some of whom may not know what security threats they are facing.
“The biggest impact is increasing the attack surface,” Meyers said, referring to the sum of entry points, the malicious actor can gain access to
companies that are most at risk: private and government health care facilities, recently distant organizations.
Nation-states fight over IP
In addition to vaccine development, state actors have also targeted companies in various intellectual property (IP) sectors, a “shopping list” of technologies to be developed that uses industrial espionage to bypass existing technology, especially in the field of artificial intelligence and machine learning.
Some nation-state actors are also interested in accessing the toolkits of cybersecurity companies that could help them in attacks such as those that occurred in the case of FireEye.
Another threat comes from bilateral agreements or purchases of joint ventures with companies from other countries, from which national actors want to benefit. And beyond intellectual property, a company’s negotiation strategies, expansion plans, and bottom line are potential targets.
Companies most at risk: clean energy, medical technology, digital farming culture, cybersecurity, mining/resources Limited, and Emerging Technologies.
Lacework Raises $ 525 Million to Automate Security and Compliance in the Cloud
Supply Chain Attacks Reaching New Heights
While supply chain attacks are nothing new, some cybersecurity experts have called 2020 the “Hack of the Decade.” A national actor has breached the network of IT software provider SolarWinds, withheld access for 264 days, and attacked customers with covert malware hidden in various software updates.
The SEC identified at least 18,000 potential victims of the attack, including top-tier companies and governments. The actor has even examined and downloaded Microsoft source code to authenticate customers.
Supply chain attacks are exceptionally damaging due to their domino effect, where penetration can lead to more subsequent multiple target breaches.
“Scope, depth, and duration I would say this was unprecedented,” Meyers said, adding that attacks on the supply chain, especially those involving software, keep you busy at night.
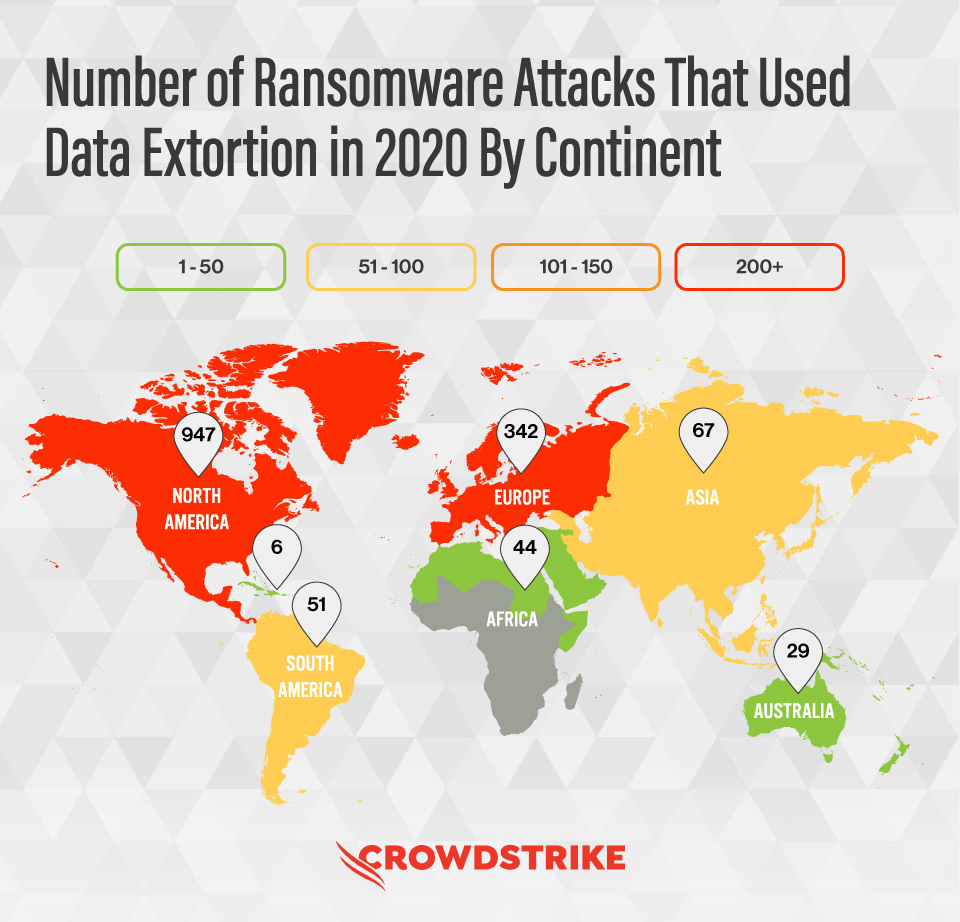
Ransomware meets extortion
Amid growing ransomware activity in 2020, integration accelerated into data extortion and extortion techniques, a practice the report warns. against, it is likely to increase this year. This reflects another recent report from data protection specialist Acronis, which stated that “2021 will be the year of extortion.”
A big part of that has been the introduction of dedicated leak sites (DLS), posts on the dark web where malicious actors, with evidence, will increase pressure on targets to meet ransom demands, with evidence from the exact data they stole.
One notable example was the attack on the New York-based law firm Grubman Shire Meiselas & Sack. The criminal group in charge dropped posts stating that it contained files on businesses and celebrities, including Madonna, Bruce Springsteen, Facebook, and eventually a 2.4GB file containing Lady Gaga’s legal documents was released. In total, this approach was adopted by at least 23 major ransomware operators in 2020.
The average rescue was $ 1.1 million. Highly branded companies can generate news and rumors on social networks that add pressure to the rescue of negotiations.
Threat actors also worked together in blackmail campaigns, forming alliances such as their own “labyrinth posters”. This could evolve into the accommodation of the data of the victims of each individual in order to increase the risk of sharing and to take advantage of the negotiation of the entire elimination or destruction of the stolen data. New variants and ransomware families have also been introduced, and a ransomware actor has been launched as a service (RAAS) (RAAS).
The report also includes the increased use of access agents, in which the hackers who gain access from the backend to companies simply contact the malware actors directly, eliminating the time it takes to identify targets and revoke access to access which allows you to deploy more malware faster.
Businesses most at risk: Although most ransomware operations are opportunistic, the industrial, engineering and manufacturing sectors were particularly affected in 2020. The technology and retail sectors are also at high risk.
How enterprises can defend against threats
According to Meyers, these are the five things enterprises should be doing:
- Secure the enterprise. This means following best practices and having multiple safeguards, including solid vulnerability management, consistent patch cycles, and “the principle of least privilege.”
- Prepare to defend. CrowdStrike recommends a 1-10-60 rule: Identify an attack within one minute, respond to it within 10 minutes, investigate it, and prevent the attacker from carrying out their objective within one hour. Either cross-layer detection (XDR) or endpoint detection and response (EDR) should be in place, according to Meyers.
- Have a next-gen solution. Antivirus needs to have seen a threat before, but machine learning-based solutions can decipher threats without having ever seen them. This difference is crucial with the growing rate of ransomware today.
- Training and practice. Get executives, directors, and board members together and develop a response plan. Know everyone you’ll need to call and don’t wait to handle attacks on the fly.
- Intelligence. Be aware of the threats, their techniques, and tools, as well as which specific threats target your industry and geolocation.